Patriot Tech Services Inc. Blog
There is always the possibility that you have been involved with a data breach and you simply have not been contacted by the affected party. Plus, if a hacker has managed to crack a website or service without being detected, you wouldn’t be notified in any case, either. Ask yourself this question: if I were to be involved with a data breach, how would I know it, and what can I do about it? And what is my data being used for anyway?
You might be surprised by some of the security breaches and vulnerabilities out there, including some for apps that you would never suspect, like Windows’ Calculator application. Hackers are always looking for new ways to infect endpoints, and nothing exemplifies this better than this particular threat, one which utilizes the Windows 7 calculator app to launch attacks against Microsoft operating systems.
Let’s begin by making one thing abundantly clear—all businesses and industries could potentially be targeted by ransomware, regardless of their size or target audience. However, as of late, some industries have been targeted more and more. Let’s examine some of the commonly targeted industries that ransomware is frequently waged against.
Let me ask you a few questions—first, how confident are you that you could spot an online ruse, and second, did you know there’s a stain on your shirt right now?
Did you look?
If so, you’ve just fallen for the school playground version of social engineering, a serious threat. Let’s discuss the kind that you’re more likely to see in terms of your business’ cybersecurity.
As a business professional, it’s your responsibility to protect your company’s digital assets from cybercrime, but the path forward is not always so easy or clear-cut. Without a thorough knowledge and expertise of IT security at your disposal, it can be challenging to protect your infrastructure as adequately as it needs to be. Here are some of the common issues that involve cybersecurity, as well as how you can address them.
Your business is your livelihood, so it only makes sense to invest in its protections so that your livelihood is secure. This will require a strategic approach. Let’s go over what your business needs to remain sufficiently secure, and what you should look for from each to get the best, most secure option.
Let’s get right to brass tacks. Your business is likely vulnerable to cybersecurity attacks. There are a whole lot of things you should be doing to protect your organization, but this one task is something you can do right now to save your business a lot of stress if something were to take down your network and cause a major disruption.
Businesses today have to deal with more potential problems than in any time in history. They are dealing with cost increases at every turn, personnel shortages, and a regulatory landscape that is always evolving. One of the biggest issues that can have a negative effect on a business is not having the processes and resources in place and working to secure its data and network. Today, we will look at five suggestions that can work to help your business keep its network and data more secure.
Security is an incredibly important part of running a business, but it’s extremely easy for busy employees to fall short of the security expectations you might place on them. This is why it is so important to train your employees on the many facets of cybersecurity. By training them, you are preparing them to tackle the plethora of challenges they will encounter throughout the workday.
How many security solutions does your organization have implemented at any given time? Traditionally, businesses have implemented what we call “point solutions,” which are software tools designed to address a specific part of your security infrastructure. While this approach is certainly better than not having security at all, it presents several problems that must also be addressed in order to most effectively protect your organization.
Your company’s email is one of its most important pieces of technology, and since that is true for nearly every business, it is unfortunately one of the most utilized attack vectors used by cybercriminals. Most businesses don’t understand just how vulnerable they are if their email isn’t properly secured and do their best to keep their employees trained on how to spot potential scams.
With many people continuing to work remotely to some extent, it would be irresponsible not to acknowledge that remote work can introduce a level of risk to an organization’s cybersecurity. This makes it all the more important that this security is locked down. Let’s discuss the concept behind zero-trust security, and why it is becoming the benchmark that organizations of all sizes should meet.
Data breaches—any event where a business’ confidential data is viewed, copied, or stolen by an unauthorized person or party—are a serious problem. Unfortunately, they are also a serious problem that can be caused by no shortage of situations. Let’s review some of the causes of business data breaches so you’ll know what to keep an eye out for.
Passwords have been a primary data security measure since 1960, when MIT researcher Fernando Corbató suggested the practice—although even he is reportedly slow to take full credit. Why? Well, if you ask Corbató (and his contemporaries, who were the first to implement passwords as we’d recognize them today), the security concerns were limited.
So, have we reached the point where it would be best to replace passwords as the default authentication measure?
We’ve all seen our friends and family sharing quizzes on their social media profiles, prompting people to find out what their celebrity stage name or what Hogwarts house you would be in, or to share what their first concert experience was. These fun, lighthearted quizzes are a great way to get to know a little more about the people we’re connected with… and that’s the biggest problem.
Gauging the effectiveness of your cybersecurity can be a bit of a daunting task, especially when asking if it could make a major difference in protecting your organization’s network infrastructure. If you want to track and measure your business’ cybersecurity preparedness, here are four steps to help you perform an evaluation.
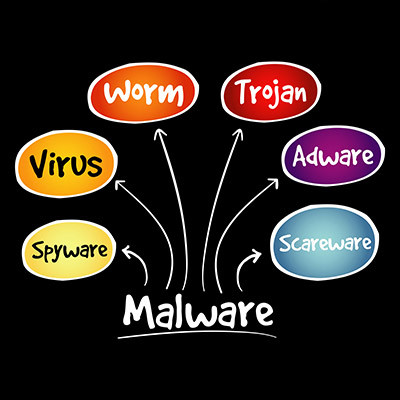
Network security could mean any number of things, but more often than not, people are using the term as a blanket statement against the dreaded idea of malware and its many forms. Today, we are discussing how vast the world of malware can be and how often you might find yourself misunderstanding what it exactly is. Knowing all this can help you identify if you have become a malware victim or not.
News & Updates
Understanding IT
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Contact Us
Learn more about what Patriot Tech Services Inc. can do for your business.
Patriot Tech Services Inc.
578 State Route 522
Wheelersburg, Ohio 45694